| As of August 2020 the site you are on (wiki.newae.com) is deprecated, and content is now at rtfm.newae.com. |
Difference between revisions of "Tutorial B5-2 Breaking DES (Straightforward)"
From ChipWhisperer Wiki
(Tag: VisualEditor) |
(Tag: VisualEditor) |
||
| Line 13: | Line 13: | ||
[[File:breaking_des.png|896x896px]] | [[File:breaking_des.png|896x896px]] | ||
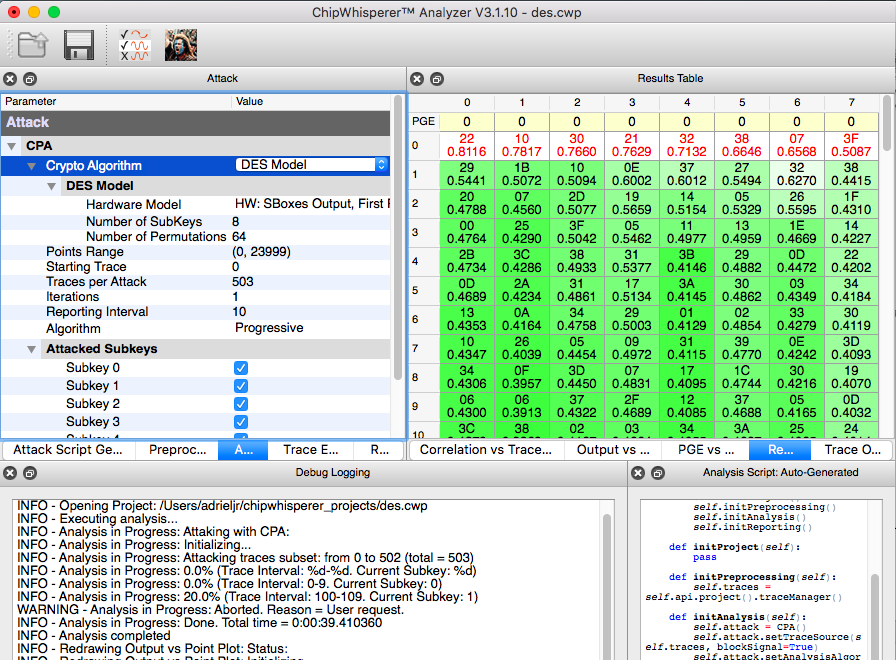
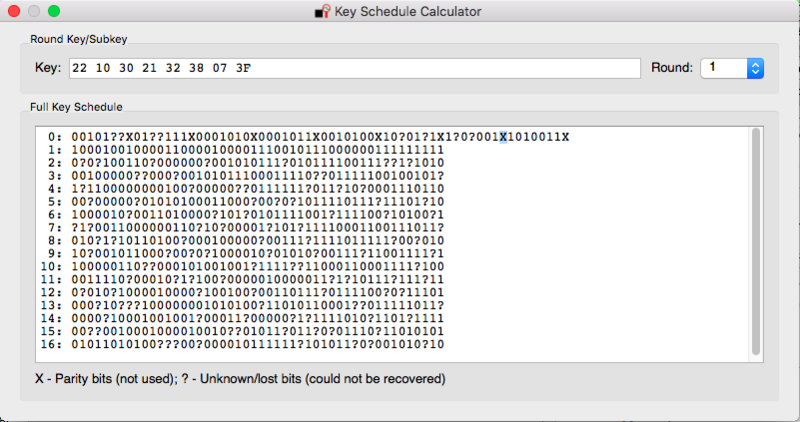
| − | Note that the attack attemps to recover the first round | + | Note that the attack attemps to recover the [[wikipedia:File:DES-key-schedule.png|first round key]], which only has 48bits ([[wikipedia:File:DES-f-function.png|8 s-box x 6 bits each]]), while the original key has 56 significant bits (64 if we count the parity bits that are irrelevant). So, if we map the first round key, obtained after the attack, to the original key (you can use the provided DES Key Schedule Tool to do it), there will still be 8 bits missing (256 combinations). |
[[File:deskeyschedulecalc.png|800x800px]] | [[File:deskeyschedulecalc.png|800x800px]] | ||
Revision as of 12:58, 14 August 2016
Follow the same procedure as in : Tutorial B5 Breaking AES (Straightforward), but:
- Flashing the DES firmware to the target device (i.e. chipwhisperer/hardware/victims/firmware/simpleserial-des/simpleserial-des-xmega.hex), instead;
and:
- Setting an appropriate 'Total Samples' and 'Offset' in the Scope Settings;
- Setting the 'Key Length (Bytes)', 'Input Length (Bytes)' and 'Output Length (Bytes)' to 8 bytes in the Target Settings;
- Setting an appropriate 8 bytes Key in the Generic Settings.
- Or, alternatively, execute the script "ChipWhisperer-Lite: DES SimpleSerial on XMEGA" to do the above steps automatically in this platform.
In the Analyzer, the only difference is to set the 'Crypto Algorithm' to DES in the Attack Settings.
Note that the attack attemps to recover the first round key, which only has 48bits (8 s-box x 6 bits each), while the original key has 56 significant bits (64 if we count the parity bits that are irrelevant). So, if we map the first round key, obtained after the attack, to the original key (you can use the provided DES Key Schedule Tool to do it), there will still be 8 bits missing (256 combinations).