| As of August 2020 the site you are on (wiki.newae.com) is deprecated, and content is now at rtfm.newae.com. |
Difference between revisions of "CW1101 ChipWhisperer-Nano"
| Line 1: | Line 1: | ||
== ChipWhisperer Nano == | == ChipWhisperer Nano == | ||
| + | |||
| + | [[File:CWNANO_RESIZE.png|800px]] | ||
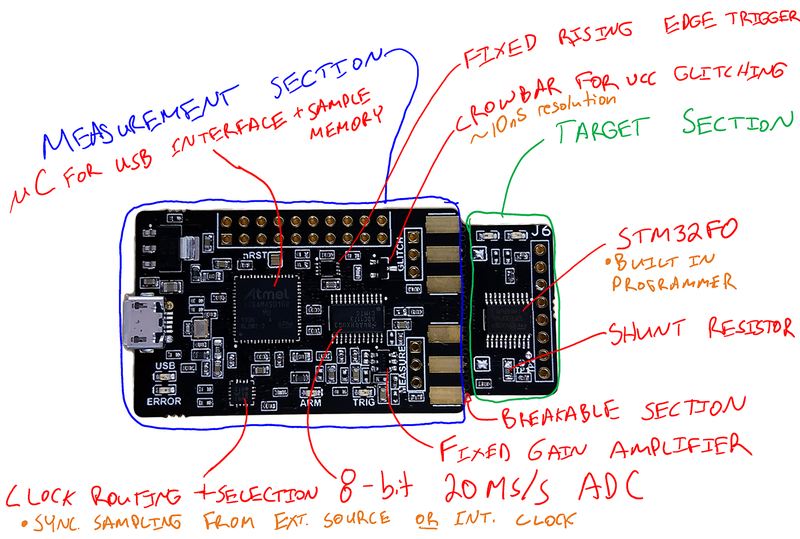
ChipWhisperer-Nano is an ultra low-cost platform for side-channel power analysis & voltage fault injection. It has the following features: | ChipWhisperer-Nano is an ultra low-cost platform for side-channel power analysis & voltage fault injection. It has the following features: | ||
# ADC capable of sampling up to 20 MS/s, using either external clock (synchronous to device) or internal clock (both synchronous and asynchronous). | # ADC capable of sampling up to 20 MS/s, using either external clock (synchronous to device) or internal clock (both synchronous and asynchronous). | ||
| − | # | + | # ADC hardware trigger uses rising-edge input and starts sampling on first device clock after trigger line going high, samples for user-configurable length. |
# STM32F030 target for loading example code onto, including a programmer built into the ChipWhisperer-Nano. | # STM32F030 target for loading example code onto, including a programmer built into the ChipWhisperer-Nano. | ||
| + | # Crowbar based VCC glitching, approx 10nS resolution on glitch width and offset (glitch offset from trigger with up to 200nS jitter). | ||
| + | |||
| + | It is primarily designed for power analysis demonstrations and training programs. It is also available as a module without a target for integration onto a target board, as one option for ChipWhisperer-Enabling your development platforms. | ||
| + | |||
| + | === Examples of Tutorials you can Run === | ||
| + | |||
| + | ChipWhisperer-Nano is a complete tutorial platform. You could run the following tutorials on it for example (using the included target): | ||
| + | |||
| + | * Perform a CPA (power analysis) attack on a textbook AES implementation. | ||
| + | * Perform a CPA attack on MBED-TLS AES implementation. | ||
| + | * Perform a DPA attack on an XOR password check. | ||
| + | * Perform a SPA attack on an RSA library. | ||
| + | * Perform a timing attack on a password check. | ||
| + | * Perform fault injection attacks to demonstrate corrupting a variable (NB: not as reliable due to limitations listed below). | ||
| + | |||
| + | If you were to attach an external target, you could also do the following: | ||
| + | |||
| + | * Perform a CPA attack on a hardware AES accelerator. | ||
| + | * Perform a power analysis attack on a FPGA target. | ||
| + | * Perform the LPC1114 tutorial. | ||
| + | |||
| + | === Limitations compared to ChipWhisperer-Lite and Pro === | ||
| + | |||
| + | The ChipWhisperer-Lite and Pro both use an FPGA for performing all clock routing, in addition to using better ADCs and analog front ends. Fundamentally, the design of the ChipWhisperer-Nano means it has the following major limitations: | ||
| + | |||
| + | * Sampling clock in external mode directly follows the input clock (no ability to multiply/divide/offset clock as in CW1173/CW1200). | ||
| + | * Sampling clock in internal mode limited to specific fixed divisions of 240 MHz PLL clock. | ||
| + | * Fixed analog front-end gain of approx 10dB. | ||
| + | * ADC limited to 20MS/s (can be overclocked slightly, up to 30MS/s but not guaranteed). | ||
| + | * No ADC offset to delay capture for some specific number of cycles after the trigger. | ||
| + | * Cannot generate clock glitching waveforms. | ||
| + | * VCC crowbar limited to coarse offset and width steps. | ||
| + | * Considerable jitter on glitch offset (due to interrupt-based source). | ||
| + | * Rising edge trigger only. | ||
| + | * Full-speed USB instead of high-speed USB. | ||
| + | |||
| + | Note that despite these limitations, ChipWhisperer-Nano can be used for attacking real devices. You can attack hardware crypto running on a microcontroller, or use power-analysis to recover a bootloader password or key. The fundamental synchronous architecture of the device (which powers all of our capture hardware tools) means it achieves considerably better performance than a regular asynchronous oscilloscope, even when that oscilloscope is running 5-20x faster. | ||
Revision as of 04:48, 1 October 2018
ChipWhisperer Nano
ChipWhisperer-Nano is an ultra low-cost platform for side-channel power analysis & voltage fault injection. It has the following features:
- ADC capable of sampling up to 20 MS/s, using either external clock (synchronous to device) or internal clock (both synchronous and asynchronous).
- ADC hardware trigger uses rising-edge input and starts sampling on first device clock after trigger line going high, samples for user-configurable length.
- STM32F030 target for loading example code onto, including a programmer built into the ChipWhisperer-Nano.
- Crowbar based VCC glitching, approx 10nS resolution on glitch width and offset (glitch offset from trigger with up to 200nS jitter).
It is primarily designed for power analysis demonstrations and training programs. It is also available as a module without a target for integration onto a target board, as one option for ChipWhisperer-Enabling your development platforms.
Examples of Tutorials you can Run
ChipWhisperer-Nano is a complete tutorial platform. You could run the following tutorials on it for example (using the included target):
- Perform a CPA (power analysis) attack on a textbook AES implementation.
- Perform a CPA attack on MBED-TLS AES implementation.
- Perform a DPA attack on an XOR password check.
- Perform a SPA attack on an RSA library.
- Perform a timing attack on a password check.
- Perform fault injection attacks to demonstrate corrupting a variable (NB: not as reliable due to limitations listed below).
If you were to attach an external target, you could also do the following:
- Perform a CPA attack on a hardware AES accelerator.
- Perform a power analysis attack on a FPGA target.
- Perform the LPC1114 tutorial.
Limitations compared to ChipWhisperer-Lite and Pro
The ChipWhisperer-Lite and Pro both use an FPGA for performing all clock routing, in addition to using better ADCs and analog front ends. Fundamentally, the design of the ChipWhisperer-Nano means it has the following major limitations:
- Sampling clock in external mode directly follows the input clock (no ability to multiply/divide/offset clock as in CW1173/CW1200).
- Sampling clock in internal mode limited to specific fixed divisions of 240 MHz PLL clock.
- Fixed analog front-end gain of approx 10dB.
- ADC limited to 20MS/s (can be overclocked slightly, up to 30MS/s but not guaranteed).
- No ADC offset to delay capture for some specific number of cycles after the trigger.
- Cannot generate clock glitching waveforms.
- VCC crowbar limited to coarse offset and width steps.
- Considerable jitter on glitch offset (due to interrupt-based source).
- Rising edge trigger only.
- Full-speed USB instead of high-speed USB.
Note that despite these limitations, ChipWhisperer-Nano can be used for attacking real devices. You can attack hardware crypto running on a microcontroller, or use power-analysis to recover a bootloader password or key. The fundamental synchronous architecture of the device (which powers all of our capture hardware tools) means it achieves considerably better performance than a regular asynchronous oscilloscope, even when that oscilloscope is running 5-20x faster.