| As of August 2020 the site you are on (wiki.newae.com) is deprecated, and content is now at rtfm.newae.com. |
Difference between revisions of "Investigating Block Cipher Modes with DPA"
(Created page with "= Block Cipher Modes = In the real world, it's a bad idea to encrypt data directly using block ciphers like AES. The goal of encryption is to produce ciphertexts that look ps...") |
(→Block Cipher Modes) |
||
| Line 2: | Line 2: | ||
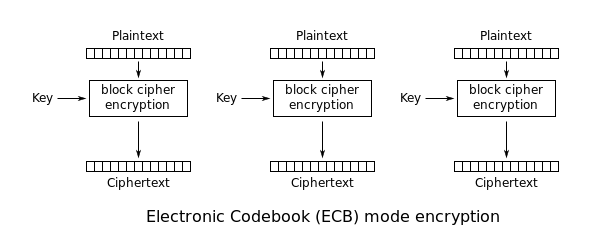
In the real world, it's a bad idea to encrypt data directly using block ciphers like AES. The goal of encryption is to produce ciphertexts that look pseudo-random: there should be no visible patterns in the output. Using a block cipher directly, encrypting the same plaintext multiple times will always result in the same ciphertext, so any patterns in the input will also appear in the output. This encryption method is called the ''Electronic Code Book'' (ECB) block cipher mode. | In the real world, it's a bad idea to encrypt data directly using block ciphers like AES. The goal of encryption is to produce ciphertexts that look pseudo-random: there should be no visible patterns in the output. Using a block cipher directly, encrypting the same plaintext multiple times will always result in the same ciphertext, so any patterns in the input will also appear in the output. This encryption method is called the ''Electronic Code Book'' (ECB) block cipher mode. | ||
| + | |||
| + | [[File:Block-Cipher-ECB.png]] | ||
To get around the weaknesses of ECB mode, there are alternative encryption methods that reuse the basic block ciphers and their core. A number of these are described [https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation on Wikipedia]. On top of ECB mode, there are 4 more block cipher modes that this attack will consider. | To get around the weaknesses of ECB mode, there are alternative encryption methods that reuse the basic block ciphers and their core. A number of these are described [https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation on Wikipedia]. On top of ECB mode, there are 4 more block cipher modes that this attack will consider. | ||
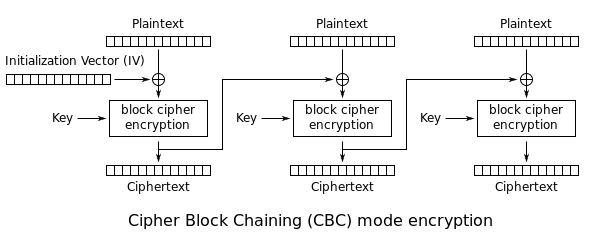
'''Cipher Block Chaining (CBC):''' The plaintext is XORed with the previous ciphertext before being encrypted. There is no ciphertext before the first plaintext, so a randomly chosen initialization vector (IV) is used instead: | '''Cipher Block Chaining (CBC):''' The plaintext is XORed with the previous ciphertext before being encrypted. There is no ciphertext before the first plaintext, so a randomly chosen initialization vector (IV) is used instead: | ||
| + | |||
| + | [[File:Block-Cipher-CBC.png]] | ||
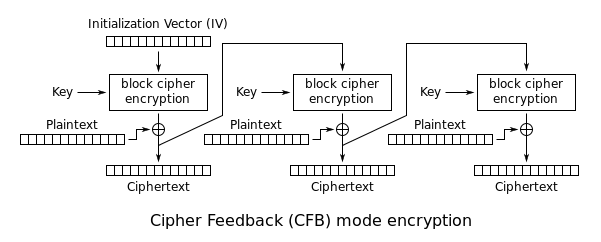
'''Cipher Feedback (CFB):''' The previous ciphertext is used as the input for the cipher. Then, the plaintext is XORed with the result to get the new ciphertext. Again, an IV is used to replace the missing ciphertext: | '''Cipher Feedback (CFB):''' The previous ciphertext is used as the input for the cipher. Then, the plaintext is XORed with the result to get the new ciphertext. Again, an IV is used to replace the missing ciphertext: | ||
| + | |||
| + | [[File:Block-Cipher-CFB.png]] | ||
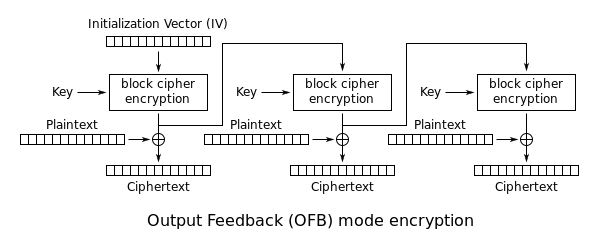
'''Output Feedback (OFB):''' An IV is repeatedly encrypted to produce a pseudo-random sequence of blocks. Then, these encryption results are XORed with the plaintexts to produce the ciphertexts: | '''Output Feedback (OFB):''' An IV is repeatedly encrypted to produce a pseudo-random sequence of blocks. Then, these encryption results are XORed with the plaintexts to produce the ciphertexts: | ||
| + | |||
| + | [[File:Block-Cipher-OFB.png]] | ||
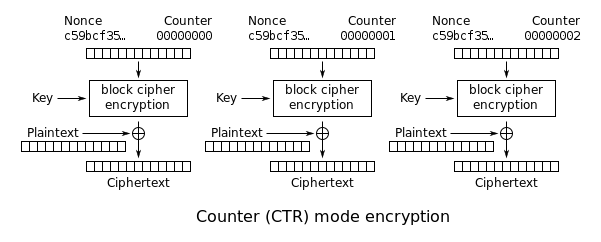
'''Counter (CTR):''' An incrementing counter repeatedly encrypted to produce a sequence of blocks, which are XORed with the plaintexts to produce the ciphertexts: | '''Counter (CTR):''' An incrementing counter repeatedly encrypted to produce a sequence of blocks, which are XORed with the plaintexts to produce the ciphertexts: | ||
| − | + | [[File:Block-Cipher-CTR.png]] | |
All four of these modes share the same quality: if the same plaintext block is encrypted multiple times, the result will be different every time. The goal of this attack to figure out which of the five cipher modes is being used. | All four of these modes share the same quality: if the same plaintext block is encrypted multiple times, the result will be different every time. The goal of this attack to figure out which of the five cipher modes is being used. | ||
Revision as of 06:24, 25 August 2016
Block Cipher Modes
In the real world, it's a bad idea to encrypt data directly using block ciphers like AES. The goal of encryption is to produce ciphertexts that look pseudo-random: there should be no visible patterns in the output. Using a block cipher directly, encrypting the same plaintext multiple times will always result in the same ciphertext, so any patterns in the input will also appear in the output. This encryption method is called the Electronic Code Book (ECB) block cipher mode.
To get around the weaknesses of ECB mode, there are alternative encryption methods that reuse the basic block ciphers and their core. A number of these are described on Wikipedia. On top of ECB mode, there are 4 more block cipher modes that this attack will consider.
Cipher Block Chaining (CBC): The plaintext is XORed with the previous ciphertext before being encrypted. There is no ciphertext before the first plaintext, so a randomly chosen initialization vector (IV) is used instead:
Cipher Feedback (CFB): The previous ciphertext is used as the input for the cipher. Then, the plaintext is XORed with the result to get the new ciphertext. Again, an IV is used to replace the missing ciphertext:
Output Feedback (OFB): An IV is repeatedly encrypted to produce a pseudo-random sequence of blocks. Then, these encryption results are XORed with the plaintexts to produce the ciphertexts:
Counter (CTR): An incrementing counter repeatedly encrypted to produce a sequence of blocks, which are XORed with the plaintexts to produce the ciphertexts:
All four of these modes share the same quality: if the same plaintext block is encrypted multiple times, the result will be different every time. The goal of this attack to figure out which of the five cipher modes is being used.