| As of August 2020 the site you are on (wiki.newae.com) is deprecated, and content is now at rtfm.newae.com. |
Difference between revisions of "Secure CAN Demo"
(Created page with "TODO") |
|||
| Line 1: | Line 1: | ||
| − | + | The Secure CAN demo is designed to present a simple secure CAN network. You can break the security on the network with the ChipWhisperer, demonstrating how side-channel power analysis is useful in all sorts of interesting situations. This example network was used in the paper "Power Analysis and Fault Attacks against Secure CAN: How Safe Are Your Keys?" by Colin O'Flynn and Greg d'Eon, published in SAE International Journal of Transportation Cybersecurity & Privacy. | |
| + | |||
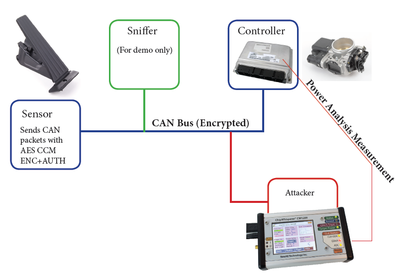
| + | The objective is to have a network as shown here, which might be similar to those used in a car: | ||
| + | |||
| + | [[File:automotive.png|400px]] | ||
| + | |||
| + | This is implemented in real life with several UFO targets with STM32Fx devices. They provide hardware CAN support, and a MBED TLS AES is used as the software AES. The attack example is portable to devices with hardware AES support (such as the STM32F415 targets). | ||
| + | |||
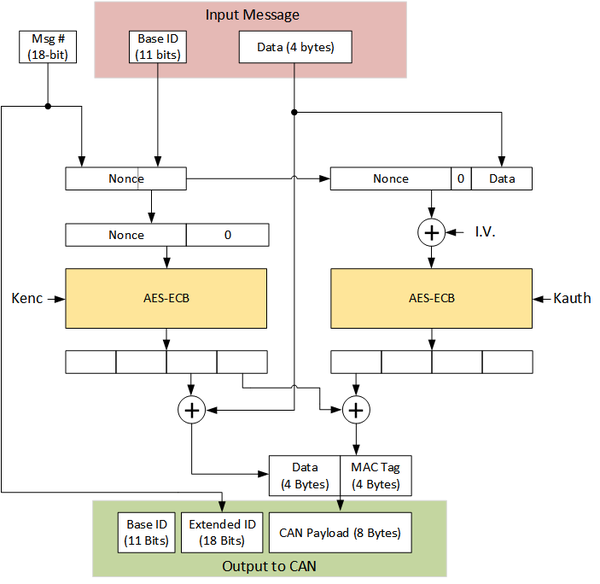
| + | The network itself uses a special secure CAN protocol. This protocol is detailed in the following figure: | ||
| + | |||
| + | [[File:securecan_network.png|600px]] | ||
| + | |||
| + | Full details are seen in the paper & the source code. The above protocol was chosen for these reasons: | ||
| + | |||
| + | * No good secure CAN using AES available as public standard. | ||
| + | * Desired to avoid CAN-FD or CAN fragmentation to simplify demonstrating the fundamental attack principles. | ||
| + | * Needed both encryption & authentication. | ||
| + | * Needed message counter for replay prevention. | ||
| + | |||
| + | The protocol is roughly based on AES-CCM. Due to the single block encrypted there is no actual count happening, but the message frame ID serves as a counter (similar to IEEE 802.15.4). | ||
| + | |||
| + | == Source Code == | ||
| + | |||
| + | For full details (including documentation) see the [https://github.com/newaetech/secure-CAN-demo Github Repository 'secure-CAN-demo']. | ||
Latest revision as of 08:23, 26 February 2018
The Secure CAN demo is designed to present a simple secure CAN network. You can break the security on the network with the ChipWhisperer, demonstrating how side-channel power analysis is useful in all sorts of interesting situations. This example network was used in the paper "Power Analysis and Fault Attacks against Secure CAN: How Safe Are Your Keys?" by Colin O'Flynn and Greg d'Eon, published in SAE International Journal of Transportation Cybersecurity & Privacy.
The objective is to have a network as shown here, which might be similar to those used in a car:
This is implemented in real life with several UFO targets with STM32Fx devices. They provide hardware CAN support, and a MBED TLS AES is used as the software AES. The attack example is portable to devices with hardware AES support (such as the STM32F415 targets).
The network itself uses a special secure CAN protocol. This protocol is detailed in the following figure:
Full details are seen in the paper & the source code. The above protocol was chosen for these reasons:
- No good secure CAN using AES available as public standard.
- Desired to avoid CAN-FD or CAN fragmentation to simplify demonstrating the fundamental attack principles.
- Needed both encryption & authentication.
- Needed message counter for replay prevention.
The protocol is roughly based on AES-CCM. Due to the single block encrypted there is no actual count happening, but the message frame ID serves as a counter (similar to IEEE 802.15.4).
Source Code
For full details (including documentation) see the Github Repository 'secure-CAN-demo'.