| As of August 2020 the site you are on (wiki.newae.com) is deprecated, and content is now at rtfm.newae.com. |
Difference between revisions of "Tutorial P1 Stream Mode and Advanced Triggering"
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | {{Warningbox|This | + | {{Warningbox|This tutorial has <b>not</b> been updated for v4.0 of ChipWhisperer.}} |
| + | |||
This tutorial will explore the ChipWhisperer Pro's custom trigger and stream features. | This tutorial will explore the ChipWhisperer Pro's custom trigger and stream features. | ||
{{TOC|limit=1}} | {{TOC|limit=1}} | ||
| − | < | + | <h2>Prerequisites</h2> |
<p> | <p> | ||
| Line 10: | Line 11: | ||
</p> | </p> | ||
| − | < | + | <h2>Introduction</h2> |
<p> | <p> | ||
| − | Unique to the [[CW1200_ChipWhisperer-Pro]]'s more advanced FPGA, the stream feature allows continuous power measurement data streaming, removing the upper limit (due to a smaller FPGA) of total samples possible. This allows to you to continuously stream data for a time period in which you can manually send data to the target to record the power response. You can later find the subsection of sample points in the streamed power trace that correspond to the encryption of data. You can now use a subsection of 128 sample points to create a custom trigger using the sum of differences | + | Unique to the [[CW1200_ChipWhisperer-Pro]]'s more advanced FPGA, the stream feature allows continuous power measurement data streaming, removing the upper limit (due to a smaller FPGA) of total samples possible. This allows to you to continuously stream data for a time period in which you can manually send data to the target to record the power response. You can later find the subsection of sample points in the streamed power trace that correspond to the encryption of data. You can now use a subsection of 128 sample points to create a custom trigger using the sum of absolute differences. This eliminates the need for the target to have code that signals the ChipWhisperer when encryption begins. The subset of points for triggering is chosen by you, so anything is possible... We will explore one possibility in this tutorial. |
</p> | </p> | ||
| − | < | + | <h2>Building the Target Code</h2> |
<p> | <p> | ||
We will begin by modifying the <code>simpleserial-aes.c</code> code with a editor of your choice. | We will begin by modifying the <code>simpleserial-aes.c</code> code with a editor of your choice. | ||
| Line 48: | Line 49: | ||
</li> | </li> | ||
<li> | <li> | ||
| − | Modify this code by commenting out | + | Modify this code by commenting out <code>trigger_high();</code> and <code>trigger_low();</code> to remove the signal produced by the target to tell the ChipWhisperer it has started the encryption process. Your c code should look like this: |
<syntaxhighlight lang="c"> | <syntaxhighlight lang="c"> | ||
/********************************** | /********************************** | ||
| Line 80: | Line 81: | ||
</li> | </li> | ||
<li> | <li> | ||
| − | Open your command line in the <code>simpleserial-aes-stream</code> directory and run the <code>make</code> command for the correct target. For example: for the XMEGA run <code>make PLATFORM=CW303</code>. This will create a <code>.hex</code> file in the same directory. This step requires avr-gcc to be set-up and added to your system path. If you have not done this go back to [[Installing ChipWhisperer]] under the <b>Required Tools</b> dropdown. | + | Open your command line in the <code>simpleserial-aes-stream</code> directory and run the <code>make</code> command for the correct target. For example: for the XMEGA run <code>make PLATFORM=CW303</code>. This will create a <code>.hex</code> file in the same directory. This step requires avr-gcc to be set-up and added to your system path. If you have not done this go back to [[Installing ChipWhisperer]] page under the <b>Required Tools</b> dropdown. |
</li> | </li> | ||
</ol> | </ol> | ||
| − | < | + | <h2>Setting up Stream Mode</h2> |
<ol> | <ol> | ||
| Line 93: | Line 94: | ||
Run the <code>Project > Example Scripts > ChipWhisperer-Lite: AES SimpleSerial on XMEGA</code> script. We will modify some of the settings. | Run the <code>Project > Example Scripts > ChipWhisperer-Lite: AES SimpleSerial on XMEGA</code> script. We will modify some of the settings. | ||
</li> | </li> | ||
| − | The modifications to the settings will allow us the use stream mode while manually sending a plain text for encryption. We will then look at the stream data and identify | + | The modifications to the settings will allow us the use stream mode while manually sending a plain text for encryption. We will then look at the stream data and identify when the block encryption takes place and what it looks like. |
<li> | <li> | ||
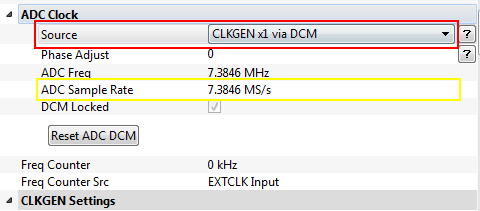
Under the <b>Scope Settings</b> find the <b>ADC Clock</b> section. Here change the <b>Source</b> setting to <code>CLKGEN x1 via DCM</code>. The <b>ADC Sample Rate</b> field should auto-populate to <b>7.3846 MS/s</b> or a number approximately equal. If the sampling rate is above 10 MS/s the streaming mode will not work as the buffer in the FPGA will overflow. | Under the <b>Scope Settings</b> find the <b>ADC Clock</b> section. Here change the <b>Source</b> setting to <code>CLKGEN x1 via DCM</code>. The <b>ADC Sample Rate</b> field should auto-populate to <b>7.3846 MS/s</b> or a number approximately equal. If the sampling rate is above 10 MS/s the streaming mode will not work as the buffer in the FPGA will overflow. | ||
| Line 100: | Line 101: | ||
</li> | </li> | ||
<li> | <li> | ||
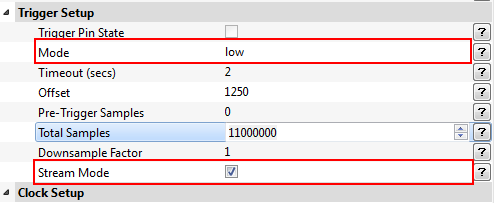
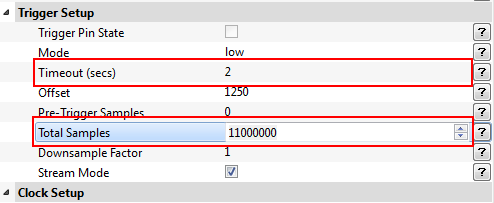
| − | Under the <b>Scope Settings</b> find the <b>Trigger Setup</b> section. Enable <b>Stream Mode</b>. The <b>Mode</b> field needs to be set to <code>low</code> so the sample capture starts right away because | + | Under the <b>Scope Settings</b> find the <b>Trigger Setup</b> section. Enable <b>Stream Mode</b>. The <b>Mode</b> field needs to be set to <code>low</code> so the sample capture starts right away because trigger line stays at low now that we have removed to code to set it high at the beginning of the encryption process. |
<br> | <br> | ||
[[File:Trigger Setup_1.PNG]] | [[File:Trigger Setup_1.PNG]] | ||
</li> | </li> | ||
<li> | <li> | ||
| − | Under the same section change the <b>Total Samples</b> field to <code>11000000</code>. This will give use a window of approximately 1.5 seconds to send a plain text and capture the power | + | Under the same section change the <b>Total Samples</b> field to <code>11000000</code>. This will give use a window of approximately 1.5 seconds to send a plain text and capture measurements of the power during encryption. |
</li> | </li> | ||
Note: The <b>Timeout (secs)</b> field needs to be set greater than the time it needs to stream the samples and a little additional time to allow for hardware communication. For example: 11 million samples take about 1.5 seconds at the sampling rate of 7.3MS/s so this field should be set to <code>2</code> seconds. You can set it higher if needed. | Note: The <b>Timeout (secs)</b> field needs to be set greater than the time it needs to stream the samples and a little additional time to allow for hardware communication. For example: 11 million samples take about 1.5 seconds at the sampling rate of 7.3MS/s so this field should be set to <code>2</code> seconds. You can set it higher if needed. | ||
| Line 112: | Line 113: | ||
</ol> | </ol> | ||
| − | < | + | <h2>Capturing the Encryption Process</h2> |
<ol> | <ol> | ||
| Line 126: | Line 127: | ||
</li> | </li> | ||
<li> | <li> | ||
| − | Repeat the previous step but before you send | + | Repeat the previous step but before you send the plain text press capture [[File:Capture One Button.PNG]] and then within 1.5 seconds send the plain text to the target for encryption. Hint: It is easier to do when you already have the plain text ready to send in the terminal and all you have to do is press send. The captured wave form should look like the following: |
<br> | <br> | ||
[[File:Stream Capture.PNG|1000px]] | [[File:Stream Capture.PNG|1000px]] | ||
| Line 132: | Line 133: | ||
Note: When pressing capture [[File:Capture One Button.PNG]], the ChipWhisperer automatically sends a plain text to the target. The plain text and response will show up in the terminal window but we are going to ignore this and focus on our manually sent plain text. | Note: When pressing capture [[File:Capture One Button.PNG]], the ChipWhisperer automatically sends a plain text to the target. The plain text and response will show up in the terminal window but we are going to ignore this and focus on our manually sent plain text. | ||
</li> | </li> | ||
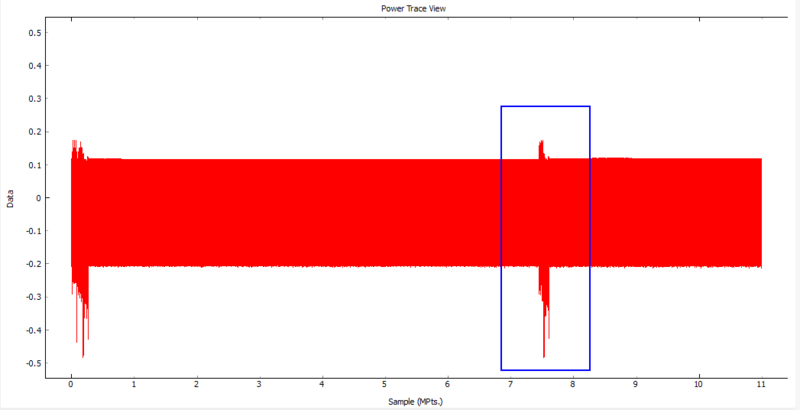
| − | Looking at the | + | Looking at the captured trace you notice that towards the end there is a series of power spikes in the sample data. |
<br> | <br> | ||
[[File:Identifying the Encryption.PNG|800px]] | [[File:Identifying the Encryption.PNG|800px]] | ||
| Line 149: | Line 150: | ||
</ol> | </ol> | ||
| − | < | + | <h2>Using a Power Pattern to Activate the Sum of Absolute Differences Trigger</h2> |
| − | We are going to use this repeating pattern to allow the [[CW1200_ChipWhisperer-Pro]] to identify when the encryption process occurs and use this to trigger our capture process. We can then use these traces to break the AES-128 encryption exactly the same as in [[Tutorial B5 Breaking AES (Straightforward)]]. | + | We are going to use this repeating pattern to allow the [[CW1200_ChipWhisperer-Pro]] to identify when the encryption process occurs and use this to trigger our trace capture process. We can then use these traces to break the AES-128 encryption exactly the same as in [[Tutorial B5 Breaking AES (Straightforward)]]. |
<br> | <br> | ||
[[File:Trigger Choice.PNG|800px]] | [[File:Trigger Choice.PNG|800px]] | ||
| Line 163: | Line 164: | ||
</li> | </li> | ||
<li> | <li> | ||
| − | When you are satisfied with the position of your trigger points press <b>Set SAD Reference from Current Trace</b> | + | When you are satisfied with the position of your trigger points press <b>Set SAD Reference from Current Trace</b> and the currently selected points will be used for the sum of absolute differences comparison carried out to activate the trigger. |
</li> | </li> | ||
</ol> | </ol> | ||
| − | Note: The Sum of Absolute Differences is carried out during the measurement process and when the total sum of absolute differences of all 128 sample points is below the threshold, the trigger is set to high to start the capture of a trace. This | + | Note: The Sum of Absolute Differences is carried out during the measurement process and when the total sum of absolute differences of all 128 sample points is below the threshold, the trigger is set to high to start the capture of a trace. This allows us to use a specific pattern to initiate the capture process without any other data from the target. The SAD equation is as follows: |
<br> | <br> | ||
<math> | <math> | ||
| Line 175: | Line 176: | ||
<ol start="3"> | <ol start="3"> | ||
<li> | <li> | ||
| − | Once you have chosen the points that initialize the trigger you can drag the selection box around and take note of the <b>SAD Reference vs. Cursor</b> value and how it changes. Notice | + | Once you have chosen the points that initialize the trigger you can drag the selection box around and take note of the <b>SAD Reference vs. Cursor</b> value and how it changes. Notice that when the selection cursor is not in the correct spot the SAD is around 10000 or more. Choose a <b>SAD Threshold</b> that will trigger only when the selected pattern is observed. For example: 5000 should work fine (If not adjust as needed). |
</li> | </li> | ||
<li> | <li> | ||
| Line 186: | Line 187: | ||
[[File:Final Capture Setup.PNG]] | [[File:Final Capture Setup.PNG]] | ||
</li> | </li> | ||
| − | We now have everything setup: The SAD Reference points will | + | We now have everything setup: The SAD Reference points will cause the trigger to be set high as soon as the SAD is below the SAD Threshold of 5000. The ChipWhisperer will record a total of 20000 samples with 500 before the reference points and 19500 during and after. We can test everything is properly setup by pressing the capture one button. You should see the same repeating pattern you saw before that represents the 10 rounds of encryption process. |
<li> | <li> | ||
Since we will be attacking the first round of the encryption process we do not need the other nine rounds. So set the <b>Total Samples</b> back to 3000. This will capture the first round and a bit of the second. | Since we will be attacking the first round of the encryption process we do not need the other nine rounds. So set the <b>Total Samples</b> back to 3000. This will capture the first round and a bit of the second. | ||
| Line 201: | Line 202: | ||
</ol> | </ol> | ||
| − | < | + | <h2>Breaking the Encryption</h2> |
We will now use the analyzer software to break the AES-128 encryption on the target and figure out the key. This section is analogous to [[Tutorial B5 Breaking AES (Straightforward) #Analyzing the Traces|Tutorial B5 Breaking AES (Straightforward)]] section of Tutorial B5. We can also use this setup for a profiling attack similar to [[Tutorial B7 Profiling Attacks (with HW Assumption)]]. | We will now use the analyzer software to break the AES-128 encryption on the target and figure out the key. This section is analogous to [[Tutorial B5 Breaking AES (Straightforward) #Analyzing the Traces|Tutorial B5 Breaking AES (Straightforward)]] section of Tutorial B5. We can also use this setup for a profiling attack similar to [[Tutorial B7 Profiling Attacks (with HW Assumption)]]. | ||
| − | < | + | <h2>Conclusion</h2> |
| + | |||
| + | In this tutorial we have learned to use two of the [[CW1200_ChipWhisperer-Pro]]'s exclusive features stream mode and SAD Trigger. The stream feature allows us the continually stream and manually send plain text to the target to observe the encryption process. Then 128 sample points that make up a unique feature of the encryption process where chosen to activate the trigger during trace capture. These two features together can be used to break the AES encryption of a device without any help from the target. | ||
| − | + | == Links == | |
{{Template:Tutorials}} | {{Template:Tutorials}} | ||
[[Category:Tutorials]] | [[Category:Tutorials]] | ||
Latest revision as of 09:05, 8 May 2018
This tutorial has not been updated for v4.0 of ChipWhisperer.
This tutorial will explore the ChipWhisperer Pro's custom trigger and stream features.
Prerequisites
This tutorial can only be completed using the CW1200_ChipWhisperer-Pro. The ChipWhisperer software and its prerequisites should be installed and the CW1200_ChipWhisperer-Pro and hardware should be connected to each other and your computer. If not, this is the page for you: Installing ChipWhisperer. This tutorial is an extension of Tutorial B1 Building a SimpleSerial Project and Tutorial B5 Breaking AES (Straightforward), which should be completed first for better understanding.
Introduction
Unique to the CW1200_ChipWhisperer-Pro's more advanced FPGA, the stream feature allows continuous power measurement data streaming, removing the upper limit (due to a smaller FPGA) of total samples possible. This allows to you to continuously stream data for a time period in which you can manually send data to the target to record the power response. You can later find the subsection of sample points in the streamed power trace that correspond to the encryption of data. You can now use a subsection of 128 sample points to create a custom trigger using the sum of absolute differences. This eliminates the need for the target to have code that signals the ChipWhisperer when encryption begins. The subset of points for triggering is chosen by you, so anything is possible... We will explore one possibility in this tutorial.
Building the Target Code
We will begin by modifying the simpleserial-aes.c code with a editor of your choice.
- Navigate to the ChipWhisperer installation directory and find the
simpleserial-aesfolder, the folder is in the...\chipwhisperer\hardware\victims\firmwaredirectory. The beginning of the file path may be different depending on the installation directory. -
Copy the
simpleserial-aesfolder into the same directory and rename it as you see fit. For example:simpleserial-aes-stream. -
Now open the
simpleserial-aes-streamfolder and rename thesimpleserial-aes.cfile to match the directory name change. For example:simpleserial-aes-stream.c -
Open the
simpleserial-aes-stream.cfile in the text editor of your choice and find this section of the code near the top./********************************** * Start user-specific code here. */ uint8_t get_pt(uint8_t* pt) { trigger_high(); aes_indep_enc(pt); /* encrypting the data block */ trigger_low(); simpleserial_put('r', 16, pt); return 0x00; } /* End user-specific code here. * ********************************/
-
Modify this code by commenting out
trigger_high();andtrigger_low();to remove the signal produced by the target to tell the ChipWhisperer it has started the encryption process. Your c code should look like this:/********************************** * Start user-specific code here. */ uint8_t get_pt(uint8_t* pt) { //trigger_high(); aes_indep_enc(pt); /* encrypting the data block */ //trigger_low(); simpleserial_put('r', 16, pt); return 0x00; } /* End user-specific code here. * ********************************/
-
Save this code, and then find the
makefilefile and open it in a text editor of your choice. Find this piece of code near the top:# Target file name (without extension). # This is the base name of the compiled .hex file. TARGET = simpleserial-aes # List C source files here. # Header files (.h) are automatically pulled in. SRC += simpleserial-aes.c
Change the
TARGET = simpleserial-aesline toTARGET = simpleserial-aes-streamand theSRC += simpleserial-aes.cline toSRC += simpleserial-aes-stream.c -
Open your command line in the
simpleserial-aes-streamdirectory and run themakecommand for the correct target. For example: for the XMEGA runmake PLATFORM=CW303. This will create a.hexfile in the same directory. This step requires avr-gcc to be set-up and added to your system path. If you have not done this go back to Installing ChipWhisperer page under the Required Tools dropdown.
Setting up Stream Mode
- Next open the ChipWhisperer software. Hopefully you know how to do this by now.
-
Run the
Project > Example Scripts > ChipWhisperer-Lite: AES SimpleSerial on XMEGAscript. We will modify some of the settings. -
Under the Scope Settings find the ADC Clock section. Here change the Source setting to
CLKGEN x1 via DCM. The ADC Sample Rate field should auto-populate to 7.3846 MS/s or a number approximately equal. If the sampling rate is above 10 MS/s the streaming mode will not work as the buffer in the FPGA will overflow.
-
Under the Scope Settings find the Trigger Setup section. Enable Stream Mode. The Mode field needs to be set to
lowso the sample capture starts right away because trigger line stays at low now that we have removed to code to set it high at the beginning of the encryption process.
-
Under the same section change the Total Samples field to
11000000. This will give use a window of approximately 1.5 seconds to send a plain text and capture measurements of the power during encryption.
The modifications to the settings will allow us the use stream mode while manually sending a plain text for encryption. We will then look at the stream data and identify when the block encryption takes place and what it looks like.
Note: The Timeout (secs) field needs to be set greater than the time it needs to stream the samples and a little additional time to allow for hardware communication. For example: 11 million samples take about 1.5 seconds at the sampling rate of 7.3MS/s so this field should be set to 2 seconds. You can set it higher if needed.
Capturing the Encryption Process
-
Now open the terminal inside the Chipwhisperer Capture Software:
Tools > Terminaland inside the Terminal window press Connect.
-
We will now send a plain text to the target for encryption to test everything is working. For example:
pAABBCCDDEEFF00112233445566778899. The target should respond with encrypted text.
-
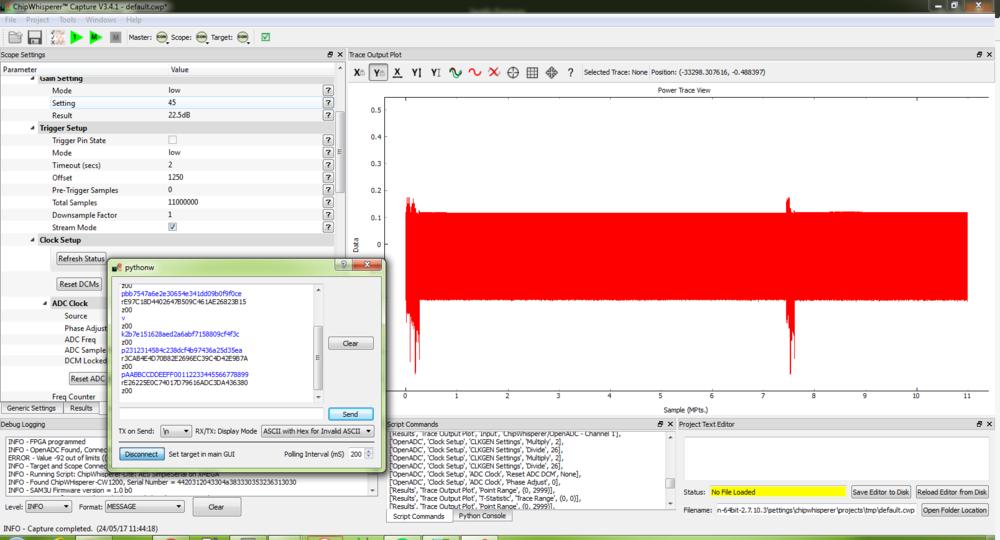
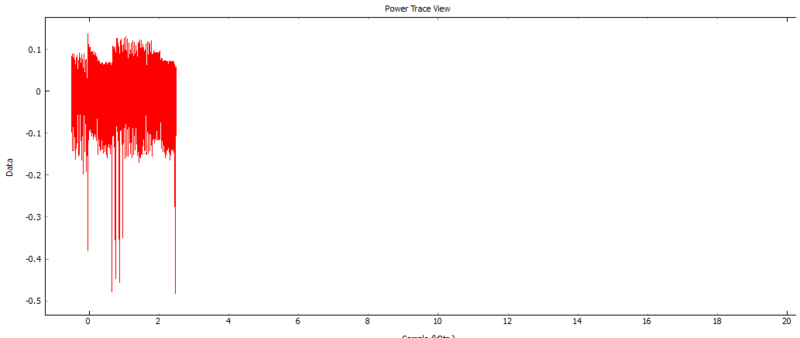
Repeat the previous step but before you send the plain text press capture
and then within 1.5 seconds send the plain text to the target for encryption. Hint: It is easier to do when you already have the plain text ready to send in the terminal and all you have to do is press send. The captured wave form should look like the following:
-
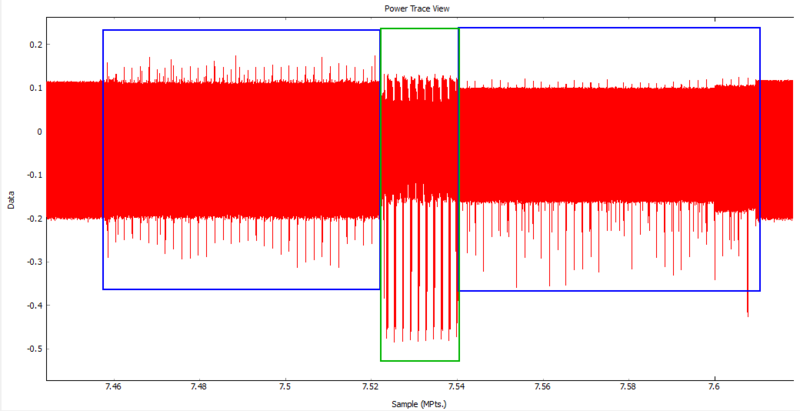
Zoom into this area and take a closer look at the power measurements. The sample data should look something like this.
Here the blue box represent the power usage during the communication and transferring of data too and from the target. The left blue box encompasses the power measurements when the target receives the plain text and the right blue box when the target sends back the encrypted text. The green box encompasses the encryption process. -
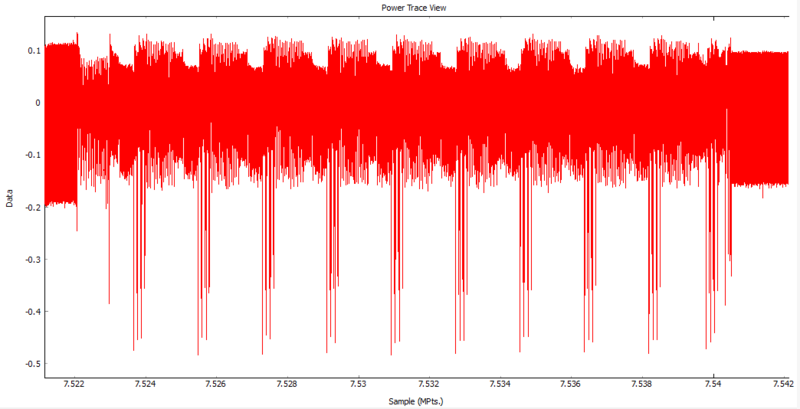
Zoom into the sample points that represent the encryption process. There should be a pattern that repeats ten times, one for each round of the AES-128 encryption.
Note: When pressing capture , the ChipWhisperer automatically sends a plain text to the target. The plain text and response will show up in the terminal window but we are going to ignore this and focus on our manually sent plain text.
Looking at the captured trace you notice that towards the end there is a series of power spikes in the sample data.
Using a Power Pattern to Activate the Sum of Absolute Differences Trigger
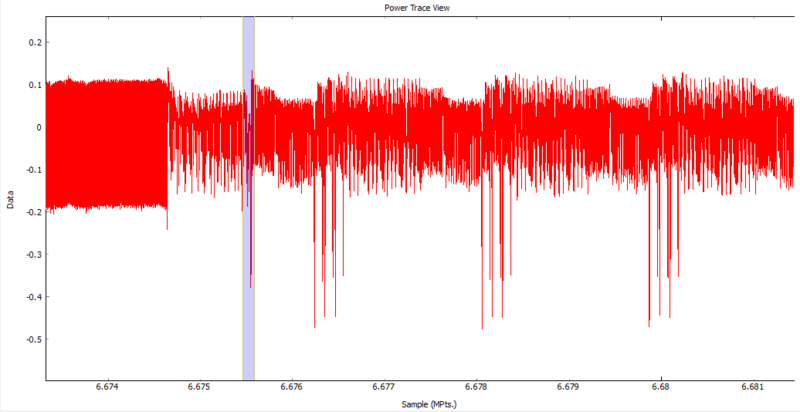
We are going to use this repeating pattern to allow the CW1200_ChipWhisperer-Pro to identify when the encryption process occurs and use this to trigger our trace capture process. We can then use these traces to break the AES-128 encryption exactly the same as in Tutorial B5 Breaking AES (Straightforward).
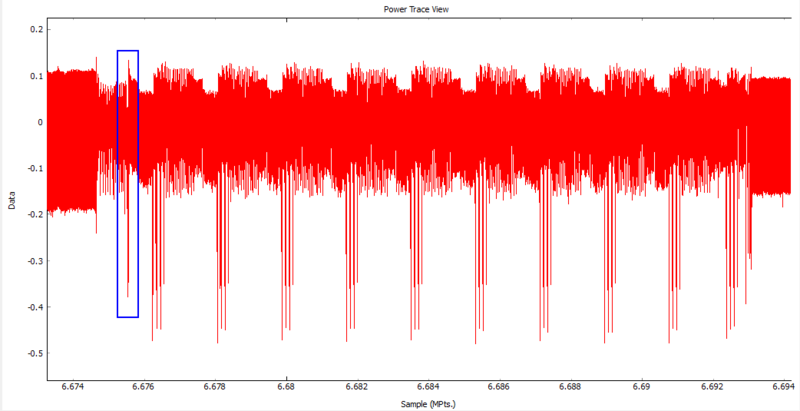
We will choose the highlighted spike and the surrounding area as our trigger as it is a unique feature that is close to the beginning of the encryption process.
-
Under Scope Settings find the SAD Trigger Module section. Here choose the 128 data point range that will be used as the trigger. Hint: You can type in a number that is close to the desired location and then click and drag the range selection box to the final position. The position numbers will be different from the ones in this tutorial because the numbers depend on when the plain text was manually sent. So just adjust the numbers as needed.
- When you are satisfied with the position of your trigger points press Set SAD Reference from Current Trace and the currently selected points will be used for the sum of absolute differences comparison carried out to activate the trigger.
Note: The Sum of Absolute Differences is carried out during the measurement process and when the total sum of absolute differences of all 128 sample points is below the threshold, the trigger is set to high to start the capture of a trace. This allows us to use a specific pattern to initiate the capture process without any other data from the target. The SAD equation is as follows:
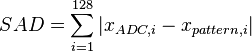
- Once you have chosen the points that initialize the trigger you can drag the selection box around and take note of the SAD Reference vs. Cursor value and how it changes. Notice that when the selection cursor is not in the correct spot the SAD is around 10000 or more. Choose a SAD Threshold that will trigger only when the selected pattern is observed. For example: 5000 should work fine (If not adjust as needed).
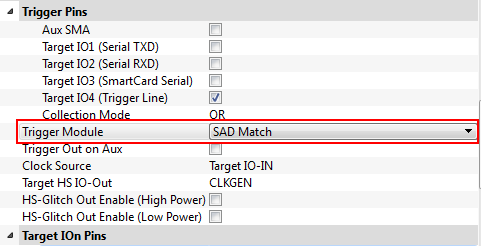
-
Under Scope Settings: CW Extra: CW Extra Settings find the Trigger Pins section and set the Trigger Module to
SAD Match.
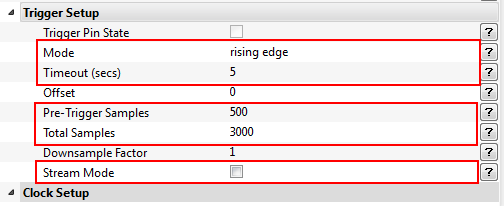
-
Now we will navigate back to the Trigger Setup section under the Scope Settings and change the Mode to
Rising Edge. The Timeout (secs) can be changed to5just to be safe, the Total Samples can be changed back to20000and the Pre-Trigger Samples can be changed to500. Note: Stream Mode should now be turned off.
-
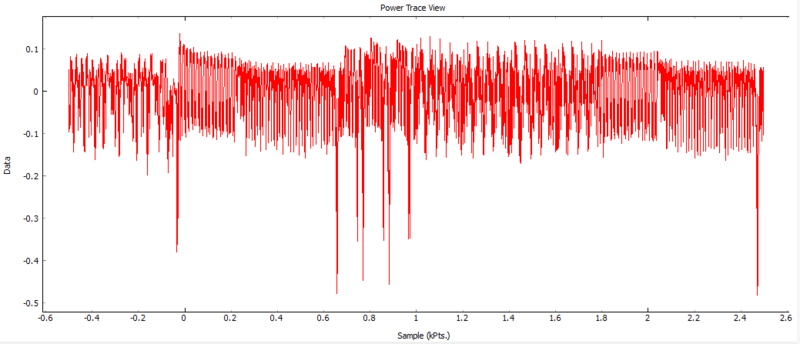
Since we will be attacking the first round of the encryption process we do not need the other nine rounds. So set the Total Samples back to 3000. This will capture the first round and a bit of the second.
Right click the graph widget and press View All (Just in case you forgot) and the wave form should look similar to this:
-
Now save the project somewhere where you can open it later and press Capture Many
button. The default of 50 captured traces should be enough to break the encryption.
We now have everything setup: The SAD Reference points will cause the trigger to be set high as soon as the SAD is below the SAD Threshold of 5000. The ChipWhisperer will record a total of 20000 samples with 500 before the reference points and 19500 during and after. We can test everything is properly setup by pressing the capture one button. You should see the same repeating pattern you saw before that represents the 10 rounds of encryption process.
Breaking the Encryption
We will now use the analyzer software to break the AES-128 encryption on the target and figure out the key. This section is analogous to Tutorial B5 Breaking AES (Straightforward) section of Tutorial B5. We can also use this setup for a profiling attack similar to Tutorial B7 Profiling Attacks (with HW Assumption).
Conclusion
In this tutorial we have learned to use two of the CW1200_ChipWhisperer-Pro's exclusive features stream mode and SAD Trigger. The stream feature allows us the continually stream and manually send plain text to the target to observe the encryption process. Then 128 sample points that make up a unique feature of the encryption process where chosen to activate the trigger during trace capture. These two features together can be used to break the AES encryption of a device without any help from the target.