| As of August 2020 the site you are on (wiki.newae.com) is deprecated, and content is now at rtfm.newae.com. |
Difference between revisions of "CW308T-SAM4L"
(→SimpleSerial Program) |
|||
| Line 13: | Line 13: | ||
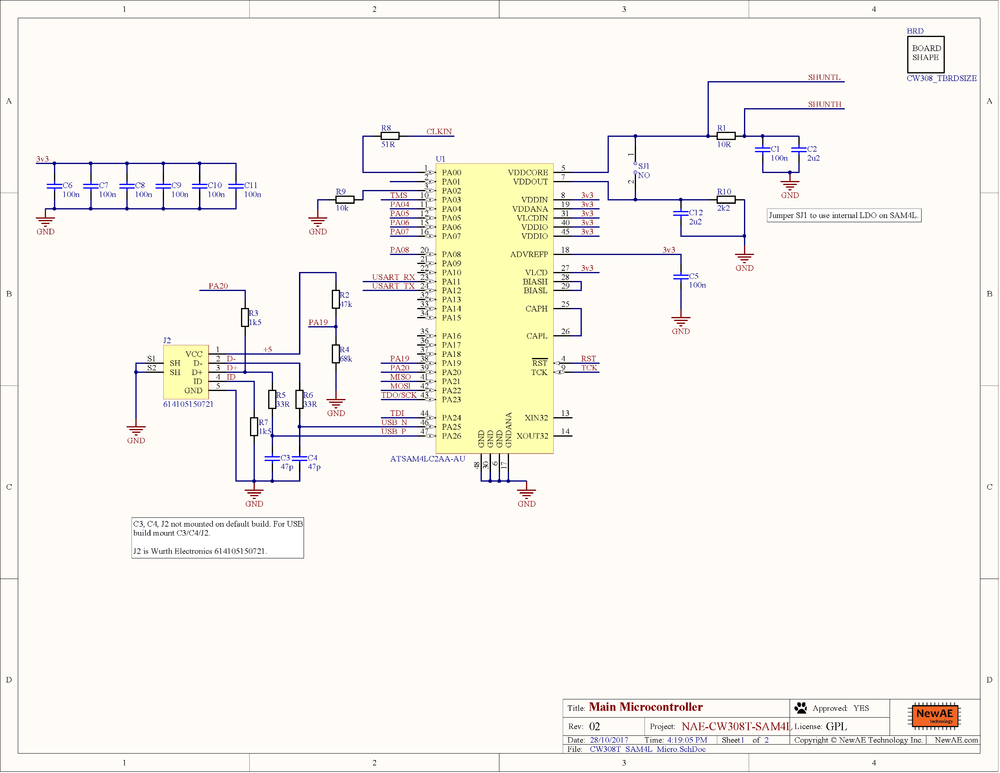
This board supports the Atmel SAM4L microcontroller. The default build has the Atmel ATSAM4LC2AA-AU, which has 128KB flash and 32KB SRAM. | This board supports the Atmel SAM4L microcontroller. The default build has the Atmel ATSAM4LC2AA-AU, which has 128KB flash and 32KB SRAM. | ||
| + | |||
| + | == Power Supply == | ||
| + | |||
| + | The Atmel SAM4L has an internal 1.8V regulator. This regulator is not used in the board, instead power for the core is supplied by an external LDO on the UFO board. Be sure to enable the 1.8V and 3.3V regulators on the UFO board for the SAM4L board to function. | ||
== Hardware AES == | == Hardware AES == | ||
| Line 34: | Line 38: | ||
== SimpleSerial Program == | == SimpleSerial Program == | ||
| − | The SimpleSerial-AES program can be built for this target. This can use either hardware crypto or a software AES. This project is currently built via the Atmel Studio IDE, and the project file is located at [https://github.com/newaetech/chipwhisperer/tree/develop/hardware/victims/firmware/simpleserial-aes/ide_projects/asf/sam4l-simpleserial-aes hardware/victims/firmware/simpleserial-aes/ide_projects/asf/sam4l-simpleserial-aes] with the ChipWhisperer release. | + | The SimpleSerial-AES program can be built for this target. This can use either hardware crypto or a software AES. This project is currently built via the Atmel Studio IDE, and the project file is located at [https://github.com/newaetech/chipwhisperer/tree/develop/hardware/victims/firmware/simpleserial-aes/ide_projects/asf/sam4l-simpleserial-aes hardware/victims/firmware/simpleserial-aes/ide_projects/asf/sam4l-simpleserial-aes] with the ChipWhisperer release. |
| + | |||
| + | If an Atmel ICE is attached as above, you should be able to build and run the example in 'debug' mode: | ||
| + | |||
| + | After this, you | ||
This uses the SAM4L HAL that is part of the build process. An automatically generated makefile can be modified to built in Linux, but currently has not been integrated into the rest of the system. | This uses the SAM4L HAL that is part of the build process. An automatically generated makefile can be modified to built in Linux, but currently has not been integrated into the rest of the system. | ||
| + | |||
| + | === Adjusting Hardware AES === | ||
| + | |||
| + | Inside the file ''hwaes.c'' you will find the AES hardware initilization. This is given in the following code sample: | ||
| + | |||
| + | <syntaxhighlight lang=c> | ||
| + | void aes_init(void) | ||
| + | { | ||
| + | periclk_aesa_init(); | ||
| + | SCIF->SCIF_GCCTRL[AESA_GCLK_NUM].SCIF_GCCTRL = SCIF_GCCTRL_OSCSEL(GENCLK_SRC_CLK_CPU) | SCIF_GCCTRL_CEN; | ||
| + | |||
| + | /* AES Enable */ | ||
| + | AESA->AESA_CTRL = AESA_CTRL_ENABLE | AESA_CTRL_NEWMSG; /* Enable, auto-accept new messages */ | ||
| + | |||
| + | //Use with debugger to check PARAMETER register value | ||
| + | //volatile uint32_t param = AESA->AESA_PARAMETER; | ||
| + | |||
| + | /* AES Mode */ | ||
| + | AESA->AESA_MODE = AESA_MODE_ENCRYPT | (AESA_MODE_CTYPE(0x0F)); /* Encrypt Mode, with all countermeasures */ | ||
| + | //AESA->AESA_MODE = AESA_MODE_ENCRYPT; /* Encrypt Mode, without countermeasures */ | ||
| + | |||
| + | /* Setup random seed for countermeasures to work */ | ||
| + | AESA->AESA_DRNGSEED = 0xDEADBEEF; //A very random number | ||
| + | } | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | Note there are two options shown, where countermeasures can be enabled or disabled. You can see the SAM4L datasheet for a description of the countermeasures. The following compares the power traces with and without countermeasures: | ||
| + | |||
| + | The following shows countermeasures enabled, you can see various execution paths taken during the encryption: | ||
| + | [[File:sam4l_wcountermeasures.png|600px]] | ||
| + | |||
| + | Compare this to the countermeasures disabled: | ||
| + | [[File:sam4l_nocountermeasures.png|600px]] | ||
| + | |||
| + | The following shows no countermeasures enabled, note the consistent execution path: | ||
| + | |||
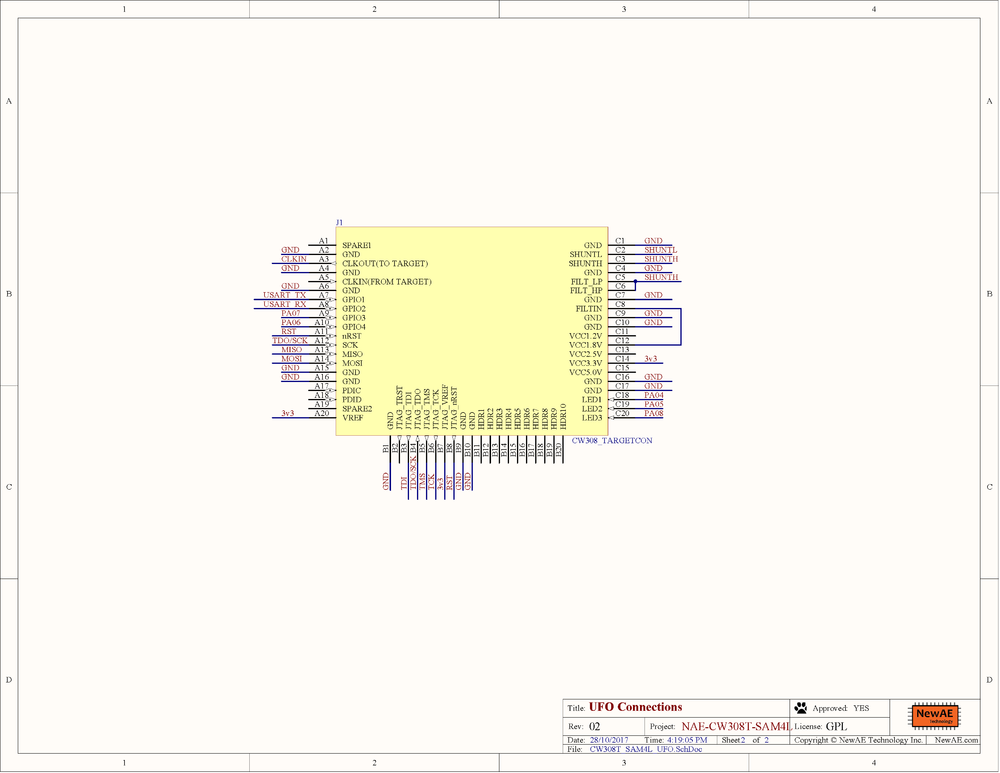
== Schematic == | == Schematic == | ||
Revision as of 18:29, 30 October 2017
| CW308T-SAM4L | |
|---|---|
 | |
| Target Device | Atmel SAM4L |
| Target Architecture | ARM Cortex M4 |
| Hardware Crypto | Yes |
| Supported Apps | Simple Serial Enc/Auth |
| Status | Released |
This board supports the Atmel SAM4L microcontroller. The default build has the Atmel ATSAM4LC2AA-AU, which has 128KB flash and 32KB SRAM.
Contents
Power Supply
The Atmel SAM4L has an internal 1.8V regulator. This regulator is not used in the board, instead power for the core is supplied by an external LDO on the UFO board. Be sure to enable the 1.8V and 3.3V regulators on the UFO board for the SAM4L board to function.
Hardware AES
The SAM4L has a hardware AES module, with optional countermeasures that can be enabled.
Programming
An external programmer is needed for this target. The SAM4L has an internal bootloader you can use via an external serial port, which is not yet supported directly by the ChipWhisperer-Capture software.
JTAG Programmer
The 20-pin JTAG port (J6 on CW308 Board) can be used with the ATATMEL-ICE which is Atmel's JTAG programmer. You can use any other ARM programmer you might have as well (i.e., OpenOCD, Segger J-Link, etc).
Using Atmel SAM-BA
Atmel SAM4L has a built-in bootloader. Not this bootloader is NOT ROM-Resident - if you reprogram the device the bootloader is lost, since it is stored in flash memory. It is recommended to use an external JTAG programmer for this target, as since the bootloader is not ROM-resident it can easily be overwritten by accident (i.e., if connecting a JTAG programmer).
SimpleSerial Program
The SimpleSerial-AES program can be built for this target. This can use either hardware crypto or a software AES. This project is currently built via the Atmel Studio IDE, and the project file is located at hardware/victims/firmware/simpleserial-aes/ide_projects/asf/sam4l-simpleserial-aes with the ChipWhisperer release.
If an Atmel ICE is attached as above, you should be able to build and run the example in 'debug' mode:
After this, you
This uses the SAM4L HAL that is part of the build process. An automatically generated makefile can be modified to built in Linux, but currently has not been integrated into the rest of the system.
Adjusting Hardware AES
Inside the file hwaes.c you will find the AES hardware initilization. This is given in the following code sample:
void aes_init(void)
{
periclk_aesa_init();
SCIF->SCIF_GCCTRL[AESA_GCLK_NUM].SCIF_GCCTRL = SCIF_GCCTRL_OSCSEL(GENCLK_SRC_CLK_CPU) | SCIF_GCCTRL_CEN;
/* AES Enable */
AESA->AESA_CTRL = AESA_CTRL_ENABLE | AESA_CTRL_NEWMSG; /* Enable, auto-accept new messages */
//Use with debugger to check PARAMETER register value
//volatile uint32_t param = AESA->AESA_PARAMETER;
/* AES Mode */
AESA->AESA_MODE = AESA_MODE_ENCRYPT | (AESA_MODE_CTYPE(0x0F)); /* Encrypt Mode, with all countermeasures */
//AESA->AESA_MODE = AESA_MODE_ENCRYPT; /* Encrypt Mode, without countermeasures */
/* Setup random seed for countermeasures to work */
AESA->AESA_DRNGSEED = 0xDEADBEEF; //A very random number
}
Note there are two options shown, where countermeasures can be enabled or disabled. You can see the SAM4L datasheet for a description of the countermeasures. The following compares the power traces with and without countermeasures:
The following shows countermeasures enabled, you can see various execution paths taken during the encryption:
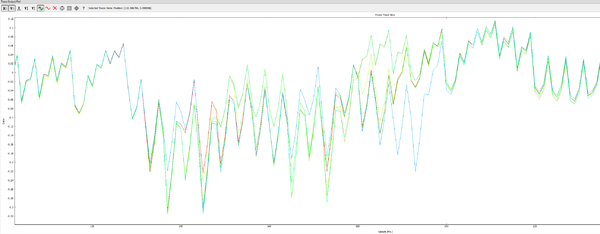
Compare this to the countermeasures disabled:
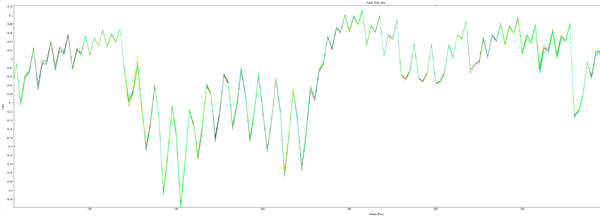
The following shows no countermeasures enabled, note the consistent execution path:
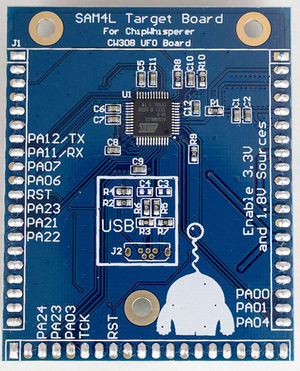
Board Layout
See GIT Repo for gerber files.